Identity-Based Encryption
Information Encryption for Email, Files, Documents and Databases
Fundamentally, the reason to use encryption is to protect data so that only a specific person (for example, bob@b.com) or a machine (for example, www.voltage.com) can access it. However, until now, encryption techniques have relied on long, randomly generated keys that must be mapped to identities using digitally-signed documents, called digital certificates – traditional PKI. The management of these certificates and the process by which they are managed, and the need to fetch a certificate before encrypting to a person or machine, has made encryption using traditional approaches very difficult for end users, costly to operate and complex for IT operations.
Identity-Based Encryption (IBE) takes a breakthrough approach to the problem of encryption key management. IBE can use any arbitrary string as a public key, enabling data to be protected without the need for certificates. Protection is provided by a key server that controls the dynamic generation of private decryption keys that correspond to public identities and the key servers base root key material. By separating authentication and authorization from private key generation through the key server, permissions to generate keys can be controlled dynamically on a granular policy driven basis, facilitating granular control over access to information in real time.
The stateless nature of IBE also dramatically simplifies operation and scaling. Key Servers can be distributed independently and geographically and key requests load balanced across them without the need to synchronize data, thus enabling high scale without growing complexity and to enable distributed and federated key management across the world easily and quickly.
The design of an Identity-Based Encryption system has its origins with Adi Shamir back in 1984, but was perfected by world-renowned cryptographers at Stanford University under US Defense funded research programs. Voltage Security was formed to commercialize the technology breakthrough. Voltage now offers solutions-based on the first secure, practical IBE system, the Boneh-Franklin IBE Algorithm., standardized under IEEE 1363.3 – the standard body for proven, public key cryptography methods.Today, IBE technology protects the data for over 100 million users world-wide, secure billions of transactions and enables more than 1,000 enterprises to embrace data-centric security easily and efficiently to enable the secure movement, use, and sharing of sensitive data at unprecedented scale.
In addition to the IEEE standard, the IETF has issued the following three RFC’s relating to the use of IBE technology:
- RFC 5091, “Identity-Based Cryptography Standard (IBCS) #1: Supersingular Curve Implementations of the BF and BB1 Cryptosystems”, describes the mathematics underlying the Voltage Identity-Based Encryption™ (IBE) approach and how to implement Voltage’s IBE cryptography.
- RFC 5408, “Identity-Based Encryption Architecture and Supporting Data Structures,” defines the components of a system that implements IBE and defines the protocols that the components use to operate securely.
- RFC 5409, “Using the Boneh-Franklin and Boneh-Boyen Identity-Based Encryption Algorithms with the Cryptographic Message Syntax (CMS),” describes how to use Voltage’s IBE within the existing standards for email encryption.
Advantages of Identity-Based Encryption
The power of IBE is in its simplicity. By using well-known identifiers, such as email addresses, as public keys, IBE enables security policies to be encoded directly into encryption and authentication methods, eliminating the need for cumbersome certificates and Certification Authorities. See the difference yourself:
The following is a RSA public key. A certificate is required to bind this key to an identity (i.e. to state that this key belongs to bob@b.com).
Public exponent:
0×10001
Modulus:
13506641086599522334960321627880596993888147560566702752448514
38515265106048595338339402871505719094417982072821644715513736
80419703964191743046496589274256239341020864383202110372958725
76235850964311056407350150818751067659462920556368552947521350
0852879416377328533906109750544334999811150056977236890927563
In contrast, this is an IBE public key. No certificate is required because the key is the identity.
Name = bob@b.com
By eliminating the need for certificates, IBE removes the hurdles of PKI: certificate lookup, lifecycle management, Certificate Revocation Lists, and cross-certification issues. IBE’s simplicity enables it to be used in ways PKI could not; IBE can be used to build security systems that are more dynamic, lightweight and scalable.
How Voltage Security Identity-Based Encryption Works
Information Encryption for Email, Files, Documents and Databases
Identity-Based Encryption (IBE) dramatically simplifies the process of securing sensitive communications. For example, the following diagram illustrates how Alice would send a secure email to Bob using IBE:
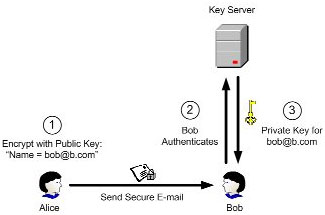
Step 1: Alice encrypts the email using Bob’s e-mail address, “bob@b.com”, as the public key.
Step 2: When Bob receives the message, he contacts the key server. The key server contacts a directory or other external authentication source to authenticate Bob’s identity and establish any other policy elements.
Step 3: After authenticating Bob, the key server then returns his private key, with which Bob can decrypt the message. This private key can be used to decrypt all future messages received by Bob.
Note that private keys need to be generated only once, upon initial receipt of an encrypted message. All subsequent communications corresponding to the same public key can be decrypted using the same private key, even if the user is offline. Also, because the public key is generated using only Bob’s email address, Bob does not need to have downloaded any software before Alice can send him a secure message.
The Math Behind IBE
The mathematical foundation of IBE is a special type of function called a “bilinear map.” A bilinear map is a pairing that has the property:
Pair( a o X, b o Y ) = Pair( b o X, a o Y )
The operator “o” is multiplication of a point on an elliptic curve by integers. While multiplication itself (e.g., calculating aoX) is easy, the inverse operation (finding a given X and aoX) is practically impossible. Two examples of bilinear maps are the Weil Pairing and the Tate Pairing.
The IBE algorithm consists of four operations:
- Setup, which initializes a key server
- Encrypt, which encrypts a message for a given user
- Key Generation, which generates a private key for a given user
- Decrypt, which given a private key, decrypts a message
